WEP Cracking via Passive Listening
The purpose of this lab is to understand and exploit the security vulnerabilities of an 802.11 WEP-secured network. You will passively collected enough WEP IV's (Initialization Vectors) to determine the WEP encryption key. After obtaining the key, you will need to masquerade as a legitimate WEP client on the network, access a server, and download a file.
Fundamental
mobile
|
WEP Cracking via Active Injection
The purpose of this lab is to continue exploring the vulnerabilities of the 802.11 WEP security protocol. It is well-known that the WEP protocol is crippled with numerous security flaws. In the WEP Cracking via passive Listening lab in the Eureka series, we explored the methods of exploiting these flaws when a large amount of data was present. However, it is unlikely that a sufficiently large data stream is present on a network when in regular usage. This makes the relatively easy WEP crack from the Basic lab considerably more difficult. In this lab, we will use more efficient techniques to continue exploiting the WEP protocol.
Fundamental
mobile
|
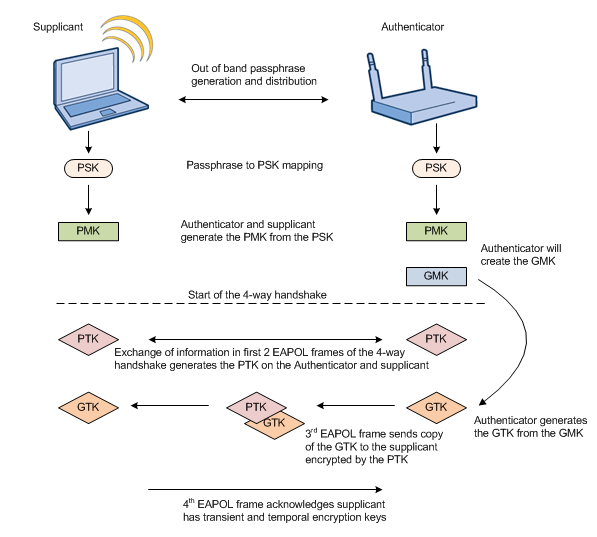
WPA-PSK Key Cracking via Handshake Capture
The first generation of the IEEE 802.11 Wired Equivalent Privacy (WEP) security standard was found to be vulnerable to various statistical weaknesses in the encryption algorithm. While at- tempts were made to correct the problem, it is still relatively simple to crack WEP and essentially obtain the password right out of thin air. As a result, the Wi-Fi Alliance created an interim stan- dard called Wi-Fi Protected Access (WPA).
However, the WPA Pre-Shared Key (PSK) mode is crackable due to a flaw that exists in the au- thentication procedure. There is a human-friendly password and a user involved. Combined with the reality that most users select poor passwords, there is an opportunity that can be exploited. The TKIP cipher is not crackable, as it is a per-packet key. However, the initialization of the TKIP, which happens during client authentication, provides an opportunity to obtain the password.
An effective way to crack WPA-PSK is to force a re-authentication of a legitimate client. By forcing an actively connected client to disconnect and reconnect, we can capture the WPA-PSK four-way handshake that protects the key exchange. A robust dictionary attack may take care of a lot of simple passwords. Consequently, it is potentially easier to crack WPA-PSK than it is to crack WEP, as we will discover in this lab.
Fundamental
mobile
|
"Unlock" Wi-Fi Protected Setup (WPS)
Wi-Fi Protected Setup, or WPS, is a push-button authentication method for WPA2 Personal-secured networks. Have you ever been connecting to a network and seen an option underneath the ``Password" field that said ``Or push the button on the router to connect?" That is WPS at work. WPS relies mainly on physical security, or the idea that a potential attacker needs to be physically present to compromise the system. However, this lab will demonstrate how a remote WPS attack is still possible.
Advanced
mobile
|
Secure your WiFi with WPA2-Enterprise
The purpose of this lab is to setup a WPA/WPA2 Enterprise (TKIP/AES + EAP-TTLS/PEAP) wireless network using FreeRadius and OpenWRT on a router. In addition, you will configure Linux/Windows/Android clients to connect to the network.
Advanced
mobile
|
Mobile Lab Platform for Users (Updated)
In this document, we first will introduce how to create a user lab platform to perform activities for our Eureka labs. Next, we will exercise with a few important wireless related commands. Lastly, we will perform a rudimentary wireless network survey with these tools and commands.
Fundamental
mobile
|
"Hide-and-Seek" in Wireless
In this basic lab, we will setup a simple wireless network with SSID hiding enabled. Students will be tasked to perform wireless network ``hide-and-seek'' (a simple wireless penetration test).
Fundamental
mobile
|
Mischievous MAC?
Carrier Sense Multiple Access (CSMA) is a probabilistic media access control (MAC) protocol in which a node verifies the absence of other traffic before transmitting on a shared transmission medium. CSMA/CA (Collision Avoidance) is a protocol for carrier transmission in 802.11 networks. In this lab, we will observe how traffic is regulated by CSMA/CA. With this knowledge, we can detect abuses and misbehavior targeted at CMA/CA at the MAC layer.
Challenging
mobile
|
Evil Twin AP Attacks and Prevention
Evil twin is a malicious access point set up to copy the identity of a real access point, hence the name twin, in order to eavesdrop and steal sensitive information. This attack will trick unsuspected users to connect to it, and from there, the attacker can perform many other attacks like man-in- the-middle or phishing websites.
Advanced
mobile
network
|
Passing on Passwords
When passwords are compromised, they can lead to unintentional data access, putting users at risk.
Fundamental
network
system
|
XSS Attack and Defense
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites.
Fundamental
network
|
Take My Coin!
A blockchain is a growing list of records, called blocks, that are linked using cryptography. Each block contains a cryptographic hash of the previous block, a timestamp, and transaction data. In this lab, we will exercise coin mining and block creation.
Fundamental
network
|
Identity Demystified
In cryptography, a public key certificate, also known as a digital certificate or identity certificate, is an electronic document used to prove the ownership of a public key. The certificate includes information about the key, information about the identity of its owner (called the subject), and the digital signature of an entity that has verified the certificate's contents (called the issuer). If the signature is valid, and the software examining the certificate trusts the issuer, then it can use that key to communicate securely with the certificate's subject.
Advanced
network
|
Crypto Flickered!
Length extension attacks can cause serious vulnerabilities when people mistakenly try to construct something like an HMAC by using hash(secret || message)}. Many hash functions are subject to length extension. Such hash functions are built around a compression function and maintain an internal state, which is initialized to a fixed constant. Messages are processed in fixed-sized blocks by applying the compression function to the current state and current block to compute an updated internal state. The result of the final application of the compression function becomes the output of the hash function. A consequence of this design is that if we know the hash of an n-block message, we can find the hash of longer messages by applying the compression function for each block that we want to add. This process is called length extension, and it can be used to attack many applications of hash functions.
Advanced
system
|
Bleeding Heart
The Heartbleed bug was a serious vulnerability in OpenSSL. The weakness allowed
attackers to steal information that would be protected in normal conditions by the SSL/TLS
encryption used to secure connections. The Heartbleed bug will take advantage of reading the
memory of the systems protected by the exploitable versions of OpenSSL. This compromises the
secret keys used to identify the service providers and to encrypt the traffic, the names and
passwords of the users and the actual content.
Advanced
network
system
|
Not-so-Personal Data
This document servers as a experiment guidance for the purpose of using Generative Adversarial Networks (GAN) on privacy attack and privacy protection.
Challenging
network
|
"Invisible" Surfing
We all need safe access to the Internet to obtain information and communicate with friends free
from technology-facilitated violent o�enses such as cyberstalking and harassment. The learning objectives of this lab are for students to be aware of personal identifiable information. Students will experiment other technologies such as Virtual Private Networks (VPNs) that protect identify information via encryption.
Advanced
network
system
|
Shell Shattered
Shellshock is a security bug in the Unix Bash shell that could
enable an attacker to cause Bash to execute arbitrary commands and gain unauthorized
access to many Internet-facing services, such as web servers, that use Bash to process
requests. The bug causes Bash to unintentionally execute commands when the commands are
concatenated to the end of function definitions stored in the values of environmental variables.
Fundamental
system
|
A “Leaky” Database
SQL injection is a code injection technique used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution. SQL injection must exploit a security vulnerability in an application's software, for example, when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. SQL injection is mostly known as an attack vector for websites but can be used to attack any type of SQL database.
Advanced
system
|
This POODLE Bites!
The Padding Oracle On Downgraded Legacy Encryption (POODLE ) attack, also known as CVE-2014-3566, is an exploit used to steal information from secure connections, including cookies, passwords and any of the other type of browser data that gets encrypted as a result of the secure sockets layer (SSL) protocol. It allows attackers to decrypt network traffic between a client and a server.
Challenging
network
system
|
Intruder Hunt
An intrusion detection system (IDS) is a device or software application that monitors a network or
systems for malicious activity or policy violations. Any intrusion activity or violation is typically
reported either to an administrator or collected centrally using a security information and event
management (SIEM) system.
Advanced
network
system
|
Walls Have Ears
The purpose of this lab is to inspired interests in mobile security by demonstrating the possibility of wireless tapping. We will explore some security vulnerabilities that are associated with wireless based VoIP services. For example, a third party may be able to intercept a phone conversation and replay it due to the openness of wireless communications.
Fundamental
mobile
|
Video Aficionado
The purpose of this lab is to understand and exploit the vulnerabilities of ``open-access'' mobile data for privacy breaches. Typically, mobile devices such as smartphones have a set of rigorous access control mechanisms (e.g., formal permission requests to access personal information) to protect private or otherwise sensitive user data. As a result, these control mechanisms prohibit a third party (e.g., an app) from directly identifying private user information. However, not all mobile data is strictly prohibited for access, e.g., power consumption of a mobile device is considered to be non-sensitive. Subsequently, it is possible to infer private information from open-access data that is available to all apps.
Challenging
mobile
|
"Pixie and Dixie vs. Mr. AI": One-Pixel Attack
The purpose of this lab is to understand and exploit vulnerabilities of deep neural networks used in Internet of Things (IoT). Image data and a trained deep neural network model are typically used to classify an image (e.g., facial recognition for authentication) on mobile and/or IoT devices. In this lab, you will prompted to pinpoint a vulnerable pixel such that changing this pixel will result in wrong classification prediction, which may confuse relevant security modules.
Advanced
mobile
|
WPA3-SAE: A Dragonfly Aims to Fix Wi-Fi’s Wings
In January 2018, WPA3 is announced to be a replacement to WPA2. The WPA3 standard replaces the pre-shared key (PSK) exchange with Simultaneous Authentication of Equals (SAE) as defined in IEEE 802.11-2016 resulting in a more secure initial key exchange in personal mode. It is also claimed that WPA3 will mitigate security issues posed by weak passwords and simplify the process of setting up devices with no display interface. However, just one year since the launch of WPA3 and researchers have unveiled several serious vulnerabilities in the wireless security protocol that could allow attackers to recover the password of the Wi-Fi network.
Advanced
mobile
|
Same, Same But Encrypted: An Enhanced Open Wi-Fi Network
Wi-Fi ``Enhanced Open'' is a new security standard for public networks based on Opportunistic Wireless Encryption (OWE). It provides encryption and privacy on open, non-password-protected networks in areas such as cafes, hotels, restaurants, and libraries. WPA3 and Wi-Fi Enhanced Open improve overall Wi-Fi security, providing better privacy and robustness against some known attacks.
Advanced
mobile
|
WPA-PSK Key Cracking with Pairwise Master Key Identifier
In our Eureka Labs series, we have a lab that crack WPA-PSK key via tricking a legitimate client into re-transmitting the EAPOL 4-way handshake frames. Differently, in this attack lab, the capture of a full EAPOL 4-way handshake is not required. The new attack is performed on the RSN IE (Robust Security Network Information Element) of a single EAPOL frame.
Advanced
mobile
|
Zombie Apocalypse: DoS Attacks and Defense
In this lab, we will launch various denial of service (DoS) attacking techniques in attempt to slow down (or complete prevent) legitimate access to a service, and learn how to adopt appropriate technologies to defend these attacks.
Advanced
network
system
|
Nothing Ethereal About Ethereum
Ethereum is a decentralized, open-source blockchain with smart contract functionality. Ether (ETH) is the native cryptocurrency of the platform. Among cryptocurrencies, Ether is second only to Bitcoin in market capitalization. Ethereum network is a peer-to-peer network consists of multiple nodes running the Ethereum client such as Geth.
Advanced
network
|
This Kerberos Never Sleeps
Kerberos is a network authentication protocol. It is designed to provide strong authentication for client/server applications by using secret-key cryptography. Kerberos works on the basis of tickets to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner. Its designers aimed it primarily at a client–server model, and it provides mutual authentication—both the user and the server verify each other's identity. Kerberos protocol messages are protected against eavesdropping and replay attacks.
Fundamental
network
|
Creating a "Toadally-Safe" Password
Passwords serve as the first line of defense when it comes to securing our online accounts. In today’s digital landscape, where cyber threats loom at every corner, it is crucial to understand the significance of creating strong and secure passwords. By doing so, we fortify our accounts against malicious attackers who seek to exploit our personal information, financial assets, and online presence. In this lab, we will evaluate the strength of passwords and discover how to improve them.
Fundamental
system
|
RansomWhale Unleashed: An Immersive Learning Experience in Ransomware Operations
Ransomware poses an ongoing and ever-evolving threat to computer security, jeopardizing the integrity of data and rendering files and systems absolutely useless. These attacks involve the utilization of malicious software to encrypt victim data, effectively holding it hostage and demanding a ransom in exchange for decrypting the files and restoring access to their crucial contents. As a result, individuals and organizations face a relentless battle to safeguard their information and mitigate the severe consequences of these relentless cybercrimes.
Advanced
network
system
|
